Hidden hard drives, loaded with data, are walking out of data centers.
Not in pockets or backpacks. They’re actually just completely missed, overlooked, data storage installed in uncommon places in common servers, firewalls and other devices.

While the classic data leak image is the malicious, cyber attack, Guardian’s data security specialists are seeing an alarming combo of plain, old-fashioned negligence and ignorance creating a huge data security gap.
It’s this lack of knowledge combined with improper documentation and the absence of a visual-based process that is letting hard drives just ride out into the world – still installed in the server hardware. Switches and other data storage devices holding IP addresses are a portal to a cyberattack.
And we are seeing these unnoticed SSDs, HDDs, PCIE, M.2s, SATADOMs and soldered-on drives everywhere.
The growing capacity of cutting-edge storage media is creating unlimited storage device possibilities. No longer is it safe to rely on past knowledge, experience and assumptions – now is the time to study up and verify the presence (or absence) of device data storage.
→ Read more: How to visually recognize modern hard drive form factors
Because it’s complex (and getting worse), trained data destruction services providers like Guardian Data Destruction are often the last checkpoint in the physical data security process. IT Asset Managers rely on us to
- recognize the uncommon,
- catch what they missed,
- educate them to prevent future errors and
- make them look better with our thoroughness.
Here’s the very true story of a recent IT asset audit of a data center for a Fortune 100 insurance company.
The Situation

Guardian was hired for an IT asset audit project that also included hard drive shredding, IT packing and logistics at a Fortune 100, multi-national insurance company. When the job was scheduled, we were told by the ITAD that hard drives had been removed from all equipment. This was confirmed by the IT Asset Manager, the onsite Point of Contact (POC), upon arrival.
Easy.
The first found, undocumented data storage: a Cisco firewall

As we audited and processed the customer’s IT assets, we came across a Cisco firewall – a very typical device for a Network Administrator, IT Asset Administrator, or field technician. It’s network hardware; not a server nor data storage.
BUT we know that this particular firewall hardware requires a front-facing, removable solid state drive (SSD) for functionality. We found the installed SSD, removed it, scanned it, reported it to the POC and then shredded it per their protocol.
Surprise data storage discovered, removed and processed: 512 GB
The second set of found, undocumented data storage: servers with internal hard drives, chips and SSDs
As the Guardian onsite audit team moved to the client’s servers, we visually confirmed that the quick-release hard drives had indeed been pulled from the front. But we discovered hard drives and SSDs inside the servers that had been completely overlooked – because no one knew they were there.
Surprise data storage discovered, removed and processed: 8000 GB

TIP: A ‘rule-of-thumb’ for hard drives: if it has video output, it has data input.
Think about your standard desktop PC – it likely has DisplayPort, VGA, DVI or HDMI outputs. From the outside, how would you know how many hard drives are inside to service those outputs? Only a look inside the chassis will inform you. We apply the same principle to rack-mountable hardware as well.

TIP: Just because there are no quick-release levers to remove a hard drive from the front of a server, it doesn’t mean that there aren’t hard drives inside.
Commonly missed hard drives are for DVR and security camera controllers. They’re typically built-in to the chassis, not meant to be serviced or extracted. Yet still holding potentially confidential data.
The final set of found, undocumented data storage: eight 10-blade servers (rack-mounted power distribution)

The last part of the audit project was the processing of eight 16-blade chassis. When we see that big box in a rack, we know we’ll be pulling apart 128 blade servers to search for hidden, unverified hard drives.
Once we inspected the first blade, we recognized a problem in the client’s hard drive accountability process. This blade server model had an allowance for five SD cards: three outside in the back and two inside. To ensure that there were no added SD cards (or any other surprises), the case had to be removed from the rack, each chassis pulled out and then 128 blades opened for a visual inspection.
Each blade revealed varied counts and sizes of internal and external SD cards.
Surprise data storage discovered, removed and processed: 10,600 GB

TIP: Inconsistency is another reason to check all servers, all laptops, all devices even if they’re the same model and year. Assume nothing.
Total revealed risk from unknown hard drives: 18,125GB
For those of you keeping score at home, that number above is EIGHTEEN THOUSAND, one hundred and twelve gigabytes of active data storage that was undetected and would have walked out of the building.
Or, said another way, EIGHTEEN TERABYTES of unknown, untracked data storage would have been carefully packed and shipped to the next destination.
In data liability terms, that’s three hundred eleven BILLION combinations of usernames and passwords. Or, 1.24 TRILLION credit card numbers. Or social security numbers.
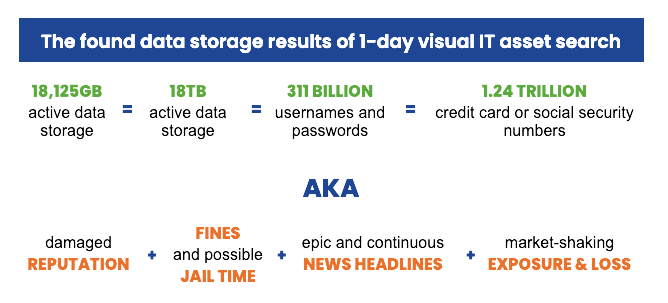
How to prevent an unknown data storage problem (and everything in the chart above)
It is no longer safe to rely on “a tech said”, or “that shouldn’t be there”. We recommend a multi-layered process to find installed hard drives and seal up giant holes in your data security:

- Always have a NAID AAA certified third party conduct your audit and e-Media data destruction.
- Create an evolving education plan that trains your IT techs and IT Asset Managers about hard drive form factors and how servers, firewalls, Apple products and more use data storage in unique ways.
- Work with your purchasing and IT departments to record all data holding devices including SD cards that are included with hardware or added to it. The more you have on your verification list, the less surprises you’ll find.
- Assume something has been missed.
- Be comfortable with removing the cover on every asset whether it’s a laptop or a server to look for data storage.
- Ask us for an onsite hard drive audit.
Your data destruction provider is the last line of defense

When it comes to data security, data privacy and data destruction, if you don’t know how to spot hard drives that are unusual form factors (shape and size), you’ve got a data security hole that is only going to get bigger. Knowing what to look for when searching for hard drive types will immeasurably shrink your data breach possibilities.
At Guardian Data Destruction, our mandate is to find data and destroy it.
- We require a visual inspection of each IT asset’s guts to ensure that the verification list and the disk sanitization software are accurate.
- We have to know how to instantly recognize any type of hard drive in a sea of tiny boxes, cables, processors, shields, chips and cards.
- We assume that we’re going to find more hard drives than are recorded.
- When we find something unusual or unexpected, we always verify with the Point of Contact before proceeding
- We believe that educating our technicians, customers and our customer’s customer is the best approach.
If you’re a VAR, ITAD or IT reseller seeking a data destruction partner that is focused on delivering cost-effective, comprehensive hard drive sanitization, contact us.
If you’re a company that’s concerned about hidden hard drives, let us introduce you to a VAR or ITAD that understands your needs.
Stay in the know, subscribe to the Guardian Data Destruction blog >



