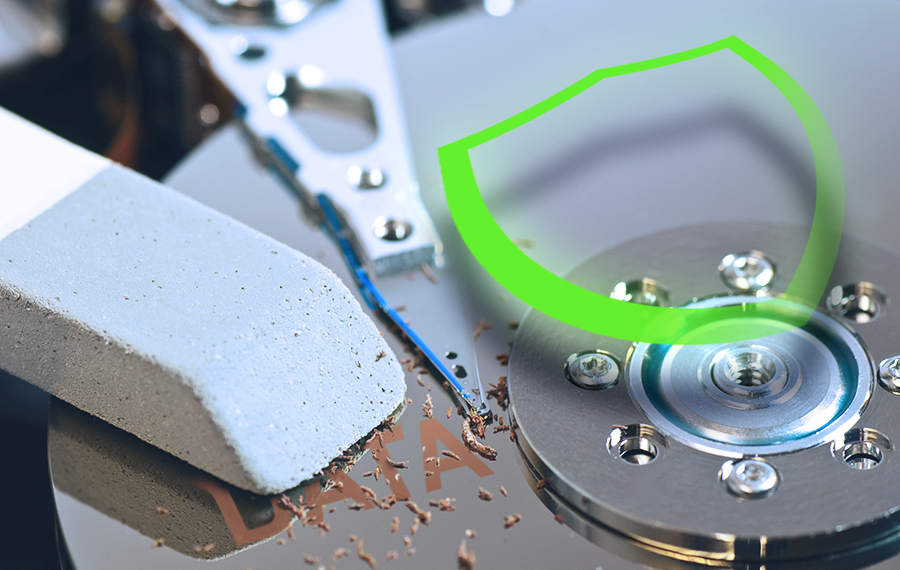
Worried about cybersecurity? Add overlooked data storage on retired enterprise IT devices to your IT asset disposition process.
Because the physical shape and size of modern hard drives are evolving, today’s hard drive can look like anything but what you’d consider to be a “classic hard drive”. Instead of the neat and tidy 3.5” or 2.5” encased SSD or platter, newer hard drive designs can look like a matchbook, a big stick of gum, RAM or blend right in with raw computer guts.

They don’t stand out as a hard drive at all.
If you miss just one of these atypical hard drives during your data destruction process…that’s a problem. If you’re missing them often (and don’t know it), you’ve got a real hole in your data security process.
Because our field service technicians and project managers run into this hide-and-stay-hidden situation all the time (read: daily and nowhere more common than with servers), Guardian trains all of our technicians to visually search for any type of data-holding component.
Data storage is often not recognized due to its location or form factor (hint: it’s not an HDD or SDD)
After the relief of knowing data storage didn’t get unknowingly shipped out, here are four common responses from onsite contacts when unknown, undocumented hard drives are found as part of our visual inspection of each and every asset.
1) “I rely on my IT techs to find all types of hard drives.”
That’s great. How up-to-date are your technicians on hard drive types and form factors? Are they required to do a visual inspection of each and every asset? Inexperienced and low-trained IT techs might not look for anything curious especially if there’s already a 2.5” or 3.5” hard drive installed. If they’re just not expecting anything else or don’t know what to look for, the visual inspection ends. Technicians assuming that hard drives require a cable may be missing hard drives with plug-in connectors.
Depending on the laptop, desktop or server, there are lots of places where newfangled hard drives can hide.
Desktops – usually straightforward.
There’s lots of space in that CPU (towers and minis) once that exterior case comes off so it’s fairly easy to see what’s been installed and what’s been added because it’s usually occupying a slot.
Laptops – this is where the fun starts.
Depending on the age and model of the unit, you’ll have a platter hard drive or a solid state drive (SSD). But, because it’s crowded in there (and sometimes very, very thin), it’s a challenge to look for additional hard drives that may have been factory installed or added later. A visual examination should include looking under the battery, under a heatshield and what’s plugged into the motherboard. The key here is to not look for another, typical hard drive.
Servers – the wild west hunt for hard drives.
Almost every server that we’ve worked on in the field is altered (and unrecorded) from its original, purchased configuration: hard drives are replaced, expanded and added in four physical areas:
- THE FRONT. Up to 24 drives are right in front of you on each server. They’re easy to find, easy to check (LEDs), easy to verify, easy to remove.
- THE BACK. Each server might have an additional 2-4 drives in the back. Inconvenient but not horrible: you will have to pull the server out on the rails to see, verify and remove.
- INTERNAL. You cannot inspect for the presence of internal hard drives if the server is in the rack. You will have to remove the server from the rack, and the rails and remove the cover. A visual inspection for extra hard drives (PCIE and M.2) should also include RISER cards which could have a PCIE slot and drive which should also be wiped.

- ONBOARD. Look for SATADOMs – SATA connection Disk On Motherboard. These super tiny (½” x ½ “ x ½”) cubes with a connector snap right into the motherboard. SATADOMs are used for machine data storage but they can also hold data and proprietary hardware information.
2) “Hard drives are easy to spot.”
Yes. And no. Read below and review the images to see if you’re up to date on this absolutely critical “I spy with my little eye” challenge.

3.5” and 2.5” standard hard drives are definitely recognizable.
Whether it’s a platter or solid state drive (SSD), these hard drives look alike – sleek little boxes that attach to the motherboard with different connectors (typically IDE, SADA or SAS).

PCIE or M.2 hard drives look like RAM so they’re often missed.
Both PCIE (“stick of gum”) and M.2 (“matchbooks”) hard drives are essentially naked or uncased 2.5” SSD hard drives. Both form factors were originally developed to save space and increase processing speed in very thin laptops and MacBook Airs. PCIE and M.2 slots are directly connected to motherboards to increase transfer rate; removing the cable removes a data bottleneck. The direct connection, small size and uncasing means that they’re often not recognized as a hard drive and mistaken for RAM.
Soldered to the board itself.
Latest generation Apple hard drives are embedded on the board. If you identify the hard drive and if the software erasure fails, the entire motherboard has to be destroyed to meet NIST standards for data sanitization.
Embedded drives are also antithetical to R2V3 and ESG initiatives and right to repair.
External hard drives and USB sticks.

Often missed and ignored as unimportant, we find too many plug-in hard drives and thumb drives in desk drawers and old laptop bags. These (very) dangerous IT assets hold user-proctored data that is ready to travel without tracking, monitoring or a disposition plan (our recommendation: shred).
3) “I rely on a serial number verification list.”
That’s the best place to begin. However, our experience has shown that records rarely reflect reality. Procurement department’s serial # records do not include changes made in the field: upgrades, expansions, replacements and swaps.
For all data destruction jobs, as the Guardian team scans IT asset serial numbers and compares it to the provided verification file, we verify what is correct and note anomalies (missing or added). This process holds true whether it’s onsite or offsite, hard drive wiping (sanitization/erasure), shredding, degaussing, pinning or mutilation.
By the end of each day, the onsite point of contact (POC) will have a list of validated, missing and added serial numbers so that the point of contact or IT asset manager has an accurate hard drive serial number record for chain of custody.
4) “My software locates all hard drives on each IT asset.”
Unfortunately, hard drive wiping software doesn’t take the place of a qualified visual inspection.
At Guardian, we use software tools as a second level of verification. The software shows you the serial # of the machine and the hard drives it finds. It doesn’t recognize or indicate hard drives that aren’t seated properly, aren’t plugged in or are defective, infected or corrupt. And, santization software is no help in finding a hard drive on a laptop, desktop or server that cannot be powered up.
Decommissioning of end-of-use IT assets depends on a visual search for data storage

When our onsite erasure technicians are given a serial # verification list for racks of laptops, desktops and servers, we have no idea what’s on those hard drives.
And, it doesn’t matter.
Our mandate is to find the data and kill it. This means….
- We require a visual inspection of each IT asset’s guts to ensure that the verification list and the disk sanitization software are accurate.
- We have to know how to instantly recognize any type of hard drive in a sea of tiny boxes, cables, processors, shields, chips and cards.
- We assume that we’re going to find more hard drives than are recorded.
Still unsure about what type of hard drives your IT equipment is hiding?
- Ask us for an onsite hard drive audit.
- Always have a NAID AAA certified third party do your e-Media data destruction.
- Create an education plan that gets your IT techs and IT Asset Managers up to speed.
- Get competitive with your IT asset verification list and software. If you find something that’s not showing up, you’re more than a winner. You’re a hard drive bloodhound. And a stellar security steward.
- Insist on visual inspections of your IT assets. It may cost more in time and effort but the hunt for the uncommon, hidden hard drive is as rewarding as a truffle hunt.
When it comes to data security, data privacy and data destruction, if you don’t know how to spot hard drives that are unusual form factors (shape and size), you’ve got a data security hole that is only going to get bigger. Knowing what to look for when searching for hard drive types will immeasurably shrink your data breach possibilities.
If you’re a VAR, ITAD or IT reseller seeking a data destruction partner that is focused on delivering cost-effective, comprehensive hard drive sanitization, contact us.
If you’re a company that’s concerned about hidden hard drives, let us introduce you to a VAR or ITAD that understands your needs.
All Guardian Data Destruction services >
Stay in the know, subscribe to the Guardian Data Destruction blog >