Explore our latest articles:
- Chain of Custody
- Compliance
- Data Destruction
- Guardian
- IT Packing & Logistics
- Processes & Procedures
- Shredding
Dear Patient, We regret to inform you that last week we learned that your personally identifiable information, including name, address, passport, date of birth, place […]
- Chain of Custody
- Compliance
- Data Destruction
- Guardian
- IT Packing & Logistics
- Processes & Procedures
- Shredding
So you’re an investment manager, RIA firm, broker/dealer, credit card company, payment processing firm, or hedge fund who has decided that it’s time to put
- Compliance
- Continuous Improvement
- Data Destruction
- Guardian
- Industry News
- Processes & Procedures
- Shredding
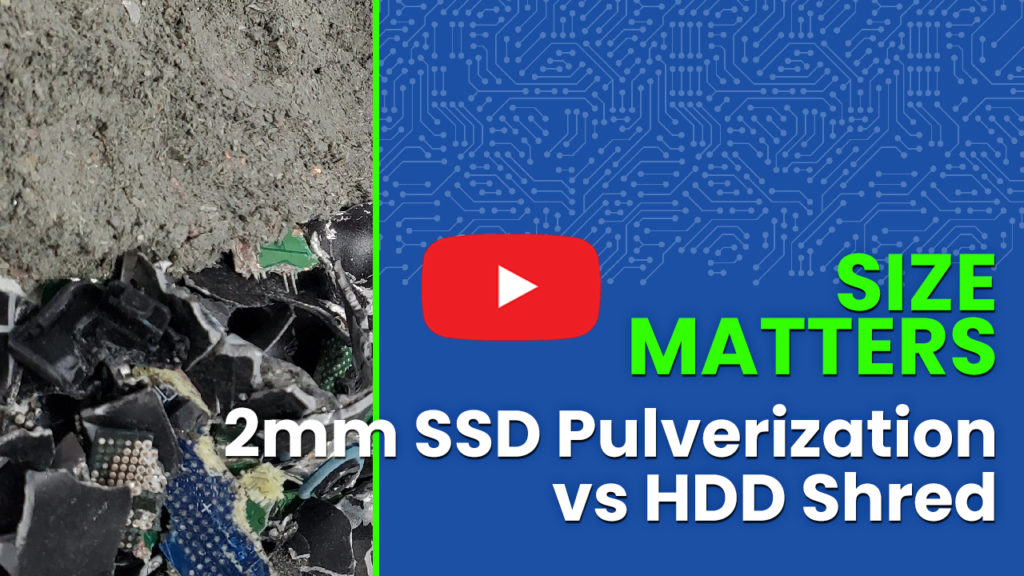
30 November, 2016 Guardian Data Destruction Launches NSA-compliant 2MM Onsite Solution for Solid State Drive Shredding(South Hackensack, NEW JERSEY) Guardian Data Destruction (“Guardian”) announces a
The slightest data breach is a risk no company can afford. Demand for safe and thorough sanitization of hard drives when assets reach end-of-life or
The practice of electronic waste (E-waste), referring to unwanted or damaged technology devices, is one of the fastest growing waste problems in the United States.
BYOD (bring your own device) is the policy where employee-owned devices are used in a business. Smartphones are the most common device used in BYOD
In IT, your server is your lifeline. It is engineered to manage, store, and transport data on a consistent and efficient basis that is critical
The failure to secure data jeopardizes the confidentiality, integrity, and accountability of any business or individual. As high profile data breaches light up news headlines,