How next-gen “dumb” devices can threaten ITAD security and disposition
Do you remember the first time you saw a new type of technology? After the oohs and aahs came the gulp as you realized that disposition policies and procedures would need to change to include this new, wondrous (and possible security risk) tech? And that your inclusion and process might already be late?
A throwback example and big shift in IT asset disposition thinking was the first iPhone released in 2007. That was followed by iPads in 2010 (who would have thought they would be a ubiquitous business device with that silly name?). Same technology, different applications.

How about the first time you saw a solid-state hard drive (SSD), specifically if it was an M.2 or PCIe format? I remember the first time I opened a server and found a SATA DOM on the motherboard or a USB key. “Holy cow, what is that? And how are we going to wipe it or destroy it to ensure data privacy compliance?”
IT devices and technology are a Pandora’s box
It is not just the new and cool stuff that needs a secure, disposition plan. It is also the old, familiar, “dumb” devices that are jumping lanes into the intelligent data storage game.
ITADs and ITAMs may remember the first time they pulled a hard drive from a printer. Plot twist! From the perspective of ITAD policy and processes, the data sanitization “watch list” abruptly changed to include all purchased printers. Now every model must be researched, evaluated and confirmed to determine if it is a data-holding asset. (And a printer.)
Here is another example of a “dumb device” that is switching sides: laptop docking stations.
Don’t wait for others to keep your IT asset management list up to date
There is no ITAD all-points bulletin about sneaky technology developments to watch out for. Most of the time, you’re learning about it through the corporate or industry grapevine (like this blog), at conferences or stumbling on it yourself.
In this case, I vaguely noticed over time that when I plugged my laptop into various docking stations, the monitor recognized my settings. Efficient? Yes. Appreciated? Definitely. Unusual? “Hmm, there’s some kind of intelligence and data storage going on here,” said my ITAD right brain to my data destruction left brain. Enter the deep dive:
Step 1: If you (ahem, me) research docking stations vs port replicators and look at the new “smart docks”.
Some laptop docking stations capture and store IP addresses when Ethernet is attached.
Step 2: You deepen the search by examining the risk factors of smart docks. And then add USB hubs to the research.
The experts are divided (for me that division increases uncertainty and boy, does that perk up my ears) Maybe the opinions are skewed by the docks the laptop is using, by brand, by functionality, by configuration.
Step 3: Add it to my ITAD list of devices to monitor for data storage capability.
As smart docks become classified as IoT devices, IT managers and ITADs need to assess the potential risk of in-use docking stations or at EOL. If the IP address is the (known) potential drawbridge over the cybersecurity moat, we all need to start paying closer attention. A docking station that opens up a laptop’s data, screen, video, audio and keystroke history is most definitely a potential threat.
And it is already happening.

A real-life hack: A docking station is physically altered to collect information
Andy Davis, research director for U.K.-based NCC Group, built a prototype hardware device that can easily be placed inside a laptop docking station to sniff traffic and, ultimately, steal sensitive corporate communications information from the laptop.

ITAD security coming from the NIST National Vulnerability Database
The Federal National Vulnerability Database (NVD) is a public repository of known vulnerability intelligence maintained by the National Institute of Standards and Technology (NIST). In addition to security checklists, software flaws, misconfigurations, product names, and impact metrics, the NVD analyzes Common Vulnerabilities and Exposures (CVEs), assigning each vulnerability a Common Vulnerability Scoring System (CVSS) score. The NVD includes helpful information to assess risk including function and exploitability.
The NIST NVD CVE (whew!) defines a vulnerability as:
LEARN MORE: Understanding the NIST National Vulnerability Database


From NIST NVD CVE-2022-4569: Lenovo ThinkPad docking station attacker code privileges
A local privilege escalation vulnerability in the ThinkPad Hybrid USB-C with USB-A Dock Firmware Update Tool could allow an attacker with local access to execute code with elevated privileges during the package upgrade or installation.
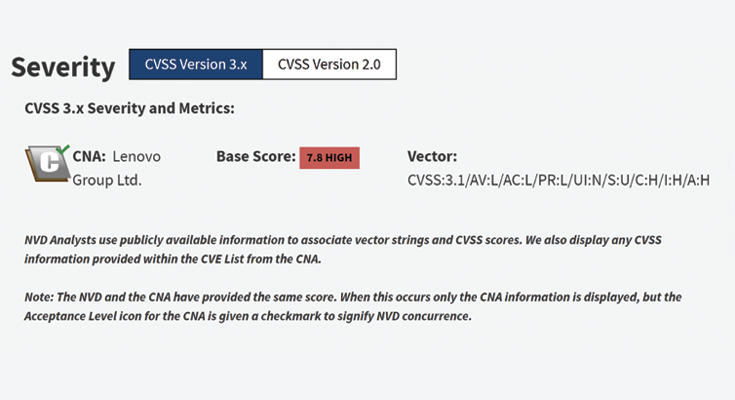
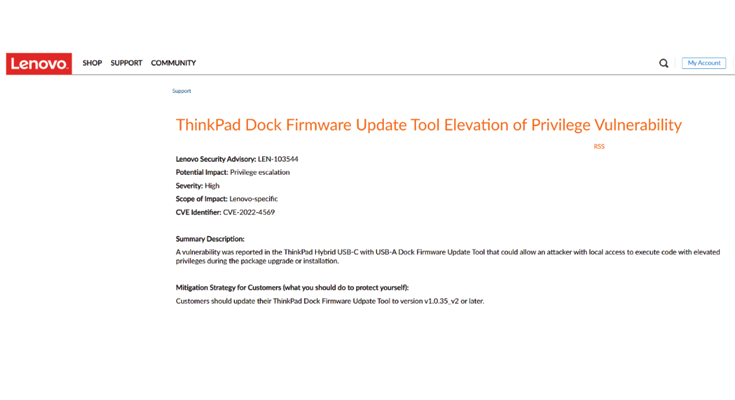
From Lenovo: ThinkPad dock firmware update tool elevation of privilege vulnerability
From Reddit: “Lenovo docking station getting its own IP address separate from the laptop and sending a small amount of data to AKAMI [sic] servers every few minutes or so.”
Discussion is ongoing and clearly divided regarding the possible risk of the Lenovo Smart Docking Station. While the docking station offers convenient connectivity and functionality, critics worry that the device’s integration with various applications and devices could lead to vulnerabilities, potentially exposing user data to hacking or unauthorized access. Additionally, there are concerns about the collection and usage of user data by Lenovo or third-party entities, raising questions about privacy and data ownership.
FOLLOW: Reddit’s Lenovo discussion here and another one here
Forget “dumb” or “smart” labels when it comes to data security
What was yesterday’s smart technology is today’s so-called dumb device. The shockingly modern cellular phone of 1983 (we’re looking at you Motorola DynaTAC 8000X) is a laughably benign version of today’s hand-held computer that also happens to include mobile communication capabilities.
So, which one is smart?
Device intelligence is defined by time and the audience.
For ITADs, ITAMs, IT departments and CTOs developing policies and processes to protect an organization’s data and privacy and upholding compliance regulations and policies, the definition of “smart” is the ability to capture and store data. Functionality, capability and age mean nothing.
That is a significantly different and broader definition of smart than an IoT device, IT hardware or tech product.
As technology continues to advance, the challenge for IT asset managers and the development of secure IT asset disposition processes lies in balancing convenience with robust security measures to mitigate data risks effectively and ensure user trust and confidence in such devices.
ITAD security starts with curiosity
Whether you stumble upon it or read a bulletin or brochure, it’s easy to recognize the new, cool IT devices. But what’s more difficult to recognize are the categorically ignored, historically “dumb” office and IT equipment and products that are evolving to handle and hold data without fanfare or notice.
“You can’t manage what you don’t know you have! A successful ITAM Program starts with awareness of the current state of the program.”
Barbara Rembiesa, CEO IAITAM

A successful ITAM program rests on the first step: knowing what you’ve got. That means cataloging new, “smart” technologies that have explicit data capturing and storage capabilities and continuously questioning and evaluating advancing categories of “dumb” devices like printers, copiers and now docking stations. If a device that was merely passing information starts saving it, it’s time to get curious. Buckle up and get ready for the data deep dive.
Read next
- Agencies and Industry Organizations IT Asset Managers Need to Know >
- Finding trusted vendors that align with your asset management policies >
- Case Study: 18K GB of unknown server data storage found in an audit>
- The future of HDDs in data centers >
Sign up for email updates to receive the latest in data security options from Guardian Data Destruction >