IT Asset Managers (ITAMs) are Rock Stars. That’s how we see it. Along with everything else on their plate, they’re managing and documenting the data destruction and data security of every IT device and peripheral. That’s a tall order.
And, there’s an opportunity for more.
With purchasing budgets and ESG initiatives coming from the C-level, IT Asset Managers are in a unique position to advocate for a small, gradual increase in hard drive erasure in place of hard drive shredding. Small steps in a hybrid approach to data destruction policy and planning can result in significant, measurable numbers in both ROI and ESG. How ITAMs can execute this, is the challenge.At IAITAM ACE 2023, Dale Hurteau, Customer Success Manager for Guardian, led a session specifically on “How to develop your Hybrid Data Destruction Policy”.
Related: Download Guardian’s Hybrid Approach to Data Destruction Policy and Planning Presentation here >
Why are data destruction policies and planning expanding to include data storage erasure?
Wiping of hard drives and SSDs is on the rise for multiple reasons:
- global market scarcity of new hard drives, SSDs and memory
- organizational pressure to extend lifecycles (when possible) to decrease costs and/or satisfy ESG/CG planning
- a realization that reuse is better than recycling which is (always) better than landfills
- residual or retained value can be credited for ROI or a charitable donation as the Social component of ESG or Carbon Credits as part of the Environmental component
- confidence in erasure software (we use only Blancco, BitRaser and Extreme Protocol unless otherwise requested)
Related: Why choose hard drive erasure over shredding >
Understand what drives your end-of-life data destruction policy

There are all kinds of criteria that drive the “how we do it here” bottom line. The most common motivators that we see across industries nationwide are fear, ESG, data security, compliance and ROI. Typically, it’s a combination of these factors depending on the company, experience and regulations.
Occasionally we run into customers where fear is the only driver. We’re asked to degauss, shred and then shred again. Kill the drive, then kill it again and again. It’s extreme but effective.
But, is it necessary?
Understanding the NIST data destruction standard

The NIST (National Institute of Standards and Technology) 800-88 standard defines media sanitization as “the general process of removing data from storage media, such that there is reasonable assurance that the data may not be easily retrieved and reconstructed.”
For the average IT Asset Manager, NIST is saying a lot without taking a definitive stand. The stand is (more than) a little fuzzy. In fact, as a general guideline, it’s specifically general.
That means the ITAM must know, “What does the NIST standard mean when my company performs data destruction? What do we degauss? Do we wipe it? Shred it? What do I do?”
The answer is a hybrid approach to developing a data destruction process that incorporates thoughtful criteria to develop a standard for data destruction methods.
Four high-level strategies to (help) determine when to shred or erase data storage as part of your data destruction policy
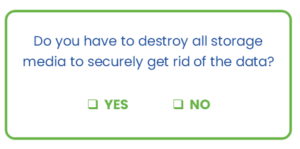
A hybrid data destruction policy incorporates multiple data destruction methods and technologies to process hard drives based on a predefined set of categories. In all cases, the goal is to securely get rid of the data.
Do you have to destroy all storage media, the HDDs and SSDs, to do so?
Start with these four high-level criteria of how to draw a line between shredding and wiping hard drives that will achieve data storage sanitization AND uphold the NIST standard. These assessments, used in combination and as a matrix or guideline for decision-making, can help develop a successful secure hybrid plan for data destruction.
1. Assess data risk by department and responsibility
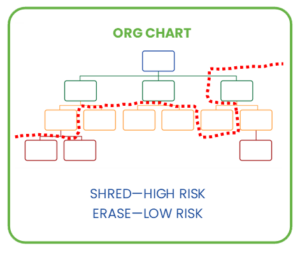
Examine every data-holding IT asset, and assign a risk level by the type of data that the department holds or has access to. 1-10? 1-5? Whatever scale works for your organization determines which computers are at low risk and can be erased vs high risk and shredded.
Examples:
- HR computers are a risk bomb: employee social security numbers, driver’s license numbers, medical, banking, etc. Very high risk.
- Help desk computers. If there’s no customer information, no critical data, then super low risk.
- Sales and Account Manager. If most of their information is cloud-based and it’s not much more information than is already on your (public) website, perhaps medium risk?
2. Assess data risk by asset ownership
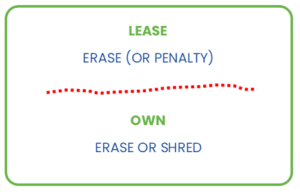
Leased IT assets typically have to be returned with their HDD or SSD drives. To determine your data destruction method, there are two primary options that are driven by a combination of risk (what type of data is on it) and cost (replacing the hard drive or risk a penalty):
- erase the leased IT asset drive
- shred or degauss the leased IT asset drive then purchase and install the replacement
An ITAD’s true story: Guardian was at an onsite shred job and we received a last-minute call from our ITAD client, “The company has already removed all the laptop hard drives. We want you to take each of the 800 drives out of their cradles before you shred the drives and then send the cradles to us. If not, it’s going to cost us an additional $15 to $18 per cradle plus the cost of the new drives for remarketing.”
The takeaway: if you have a computer or server with no hard drive, it still has value. The more components you remove from any expensive IT asset, especially for redeployment or lease return, the more money you have to put into it to make it functional. If you must shred, consider even minor savings like saving the cradles to reduce your charges and reduce landfill/recycling.
3. Assess data risk by asset age
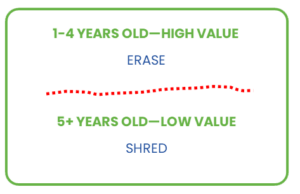
Age and value are proportional. IT assets that are less than three years older are generally better candidates for reuse and resale (ROI) calculations, therefore an excellent erasure contender!
For older devices, examine lifecycle cost. Can an aging asset provide one more year of solid service without becoming a repair or performance loss? If there’s little ROI but a high likelihood of an extended lifespan, consider erasing the HDD or SSD instead of shredding.
4. Assess data risk by asset type
Another way to draw the line between erasure and shredding is to develop a matrix that organizes the IT asset by category. If the device falls into the matrix by type, the default data destruction method is already determined. Then apply other assessments including department, age and ownership. As an example:
| IT Asset Type | Primary Data Destruction Method |
|---|---|
| Cell Phones | SHRED |
| Tablets | SHRED |
| Laptops | WIPE |
| Servers | SHRED |
| Storage Arrays | WIPE |
| Printers & Copiers | SHRED |
| Desktops | WIPE |
| Firewalls, Routers, Switches, Hubs, Remote Access Controllers | FACTORY RESET |
Don’t forget about factory reset! This is a secure alternative to shredding entire boards (and therefore nullifying the device completely) and, as we see most often, completely ignoring that firewalls, routers, switches, hubs and remote access controllers contain IP and access data that you do not want out there if the equipment is moving locations (yours, on the market or recycling). Factory resets are complex and very specific to each device so it’s imperative to have them performed by an expert.
Related: Reduce Risk in Enterprise Data Destruction: Reset Data Center Factory Defaults >
An ITAM Checklist: How to develop a hybrid approach to secure data destruction
Successful hybrid data destruction programs can benefit both ROI and ESG without compromising data security. Use this checklist to start developing your own:
☐ Understand the value of your data (you know the value of everything else!)
☐ Understand the value of your hardware. Work with your VARs, ITADs and Service Providers who remarket your assets to return a higher ROI
☐ Evaluate IT risk (department, ownership, age, type, etc) to determine best data destruction practices
☐ Understand penalties and upcharges for returning incomplete assets
☐ Be clear on management’s mindset and goals for ESG and corporate governance
☐ Include cross-department stakeholders: CEO, CFO, CTO, CMO
☐ Have a documented plan built on thoughtful risk criteria
☐ Don’t let data travel (onsite data destruction removes the risk of in-transit loss or theft)
☐ Use tools and technology developed by the experts
☐ Lean on your partners (VARs, ITADs, IT departments, data destruction providers) for best practices help
☐ Execute data destruction by NAID AAA Certified experts
☐ Outsource for third-party verification of internal processes
☐ Document everything including Chain of Custody and Certificates of Destruction (with asset serial #)
Download a PDF of this guide here >
The wrap-up on developing a secure, hybrid IT asset data destruction policy and plan

While IT asset managers aren’t landing on the moon (yet), data destruction can become a “one small step” story for your organization.
ITAMs can make a big difference.
By implementing a secure, hybrid approach to data destruction, you can make a significant, measurable ROI and ESG impact that you can report to your organization. And you can prove it. And that makes you a rock star.
For additional information specific to ESG and data destruction, dive into environmental, social and governance and view Guardian Data Destruction’s ESG statement.
For help finding an ITAD, VAR or service provider that can help you maximize ROI and ESG from the initial procurement process to disposition, ask us for a recommendation.To get a walk-thru of your IT assets to build your best hybrid data destruction program, talk to us. Whether it’s onsite shred, erasure, hyper-scale erasure, complete data center relocations or decommissioning, Guardian can help.